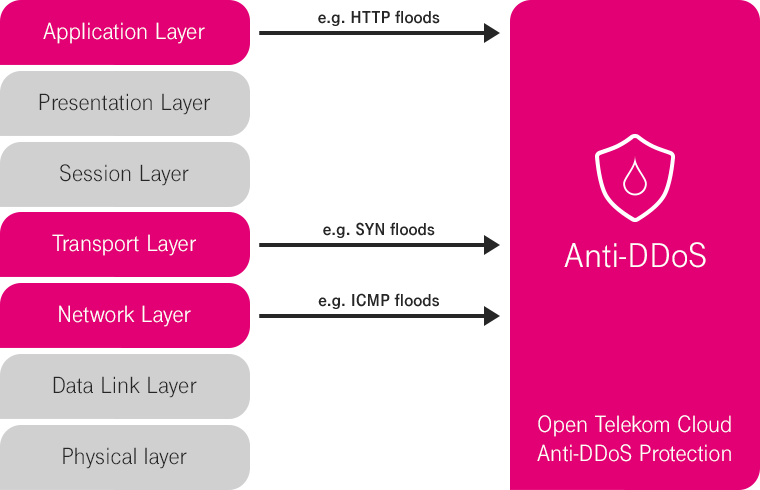
Many publicly accessible corporate websites are subject to hacker attacks. A common scenario is when a website is overloaded by a flood of requests from different IP addresses within a short period of time. This is what is known as a distributed denial-of-service attack (DDoS). The sheer amount of requests brings the website to its knees, rendering the service unavailable. For owners, this is a highly unpleasant scenario.
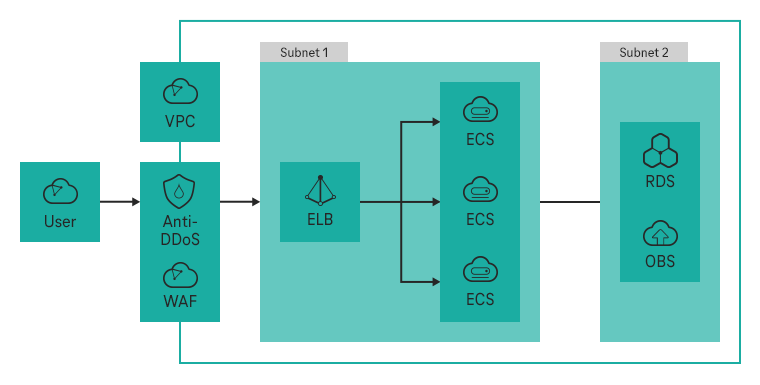
Website hosts can protect themselves from these kind of attacks with a software-based security feature: Anti-DDoS automatically detects DDoS attacks by checking incoming requests for malicious intent. In the event of an attack, it redirects spurious requests and ensures that the service remains online without sapping any additonal resources.