In today's digital age, cloud computing has become an essential part of many companies' IT strategies. Cloud infrastructures provide the flexibility, scalability and cost-efficiency that companies need to remain competitive. However, with the increasing reliance on cloud infrastructures comes the need for robust security measures to protect against threats and vulnerabilities.
As companies move more applications and data to the cloud, they face a growing risk of cyberattacks, data breaches, and compliance issues. Traditional security solutions may not be sufficient to address the unique challenges of cloud computing, such as:
- Increased attack surface: Cloud infrastructures provide a larger attack surface with more entry points for hackers and malicious actors.
- Lack of visibility and control: Conventional security solutions may not provide the visibility and control needed to protect cloud-based applications and data.
- Compliance and regulatory requirements: Cloud infrastructures must comply with regulatory requirements such as PCI DSS, HIPAA and GDPR.
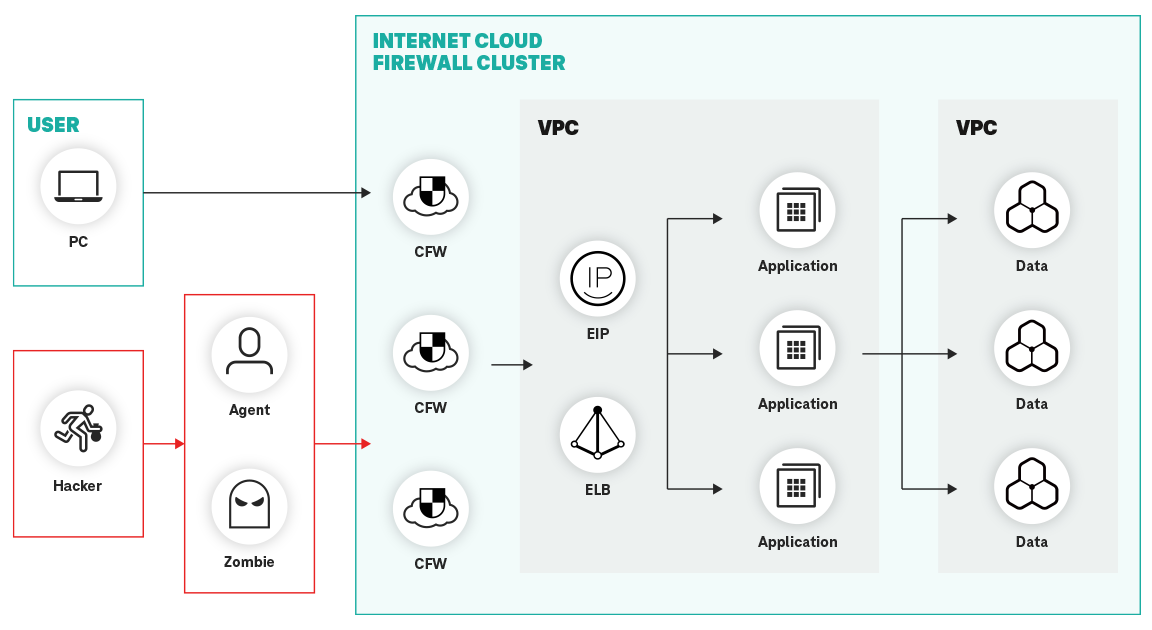
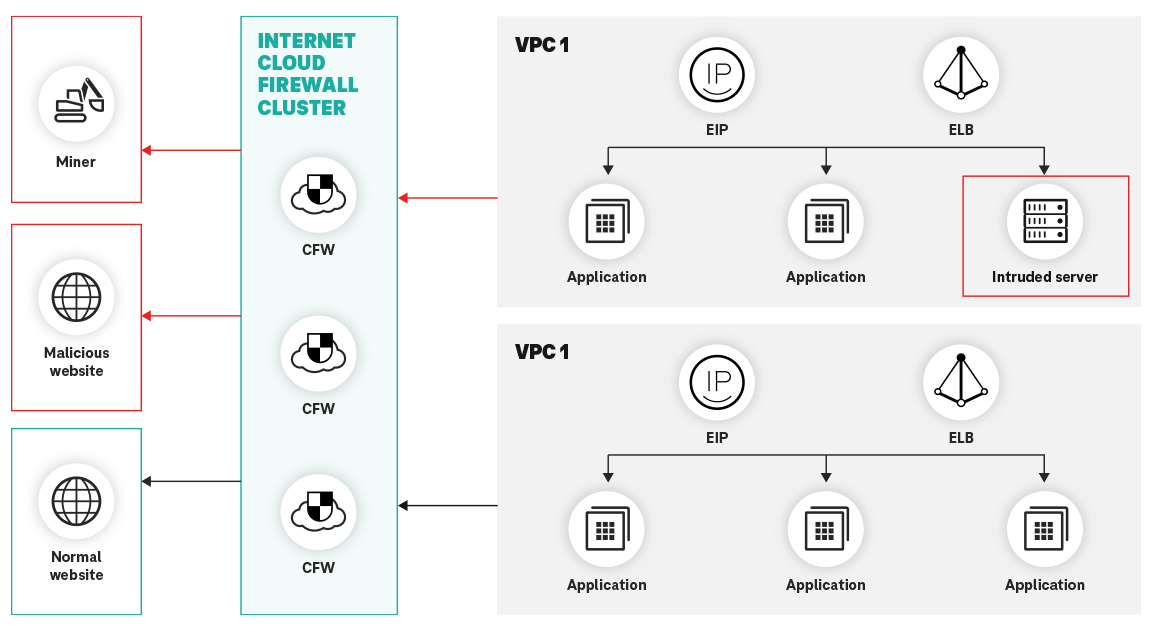
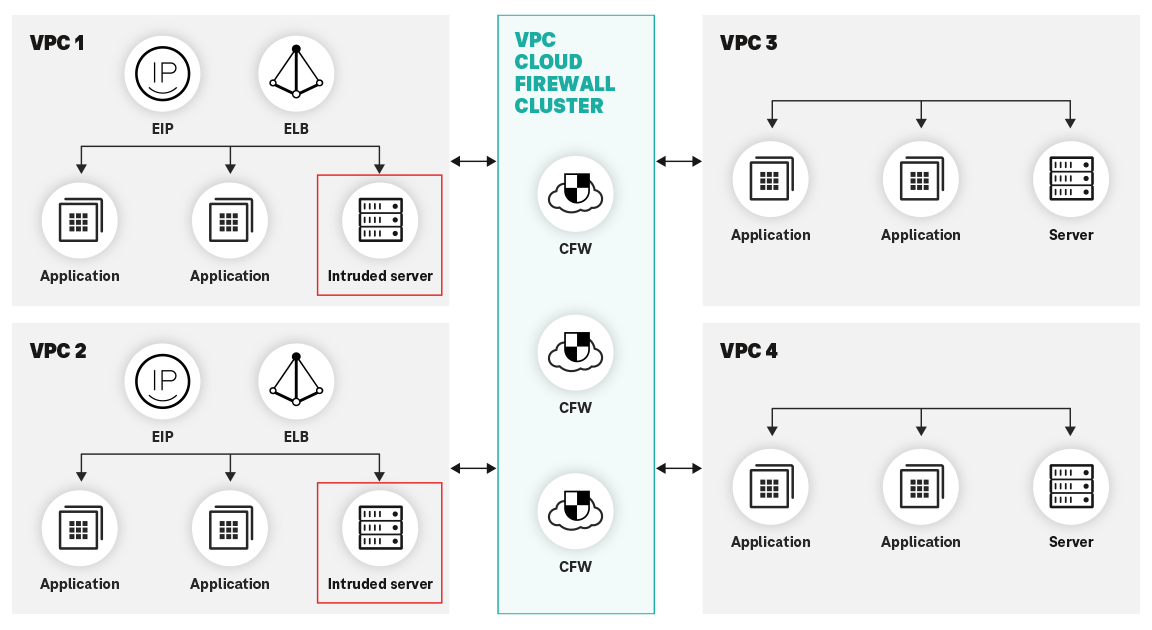
Cloud Firewall (CFW) is designed to address these challenges and provides a cloud-native firewall solution to help companies protect their cloud infrastructure from potential threats. With its advanced features and capabilities, Cloud Firewall helps you create a secure and isolated environment for your applications and data while ensuring compliance with regulatory requirements.