Who is allowed to access which data and when? How large must the dimensions of which systems be? And how do IT managers keep an overview? Designing a hybrid cloud infrastructure is a complex challenge. After all, every industry and every company have different requirements and different budgets: "Off-the-shelf solutions don’t exist here and wouldn’t make sense either. What's more, not all companies have in-house specialists who are capable of designing a complex hybrid cloud infrastructure," says Sascha Smets, Senior Product Manager Open Telekom Cloud at T-Systems. "That's why more and more companies are turning to us for our expertise. We help companies design, build and operate these kinds of IT topologies.“
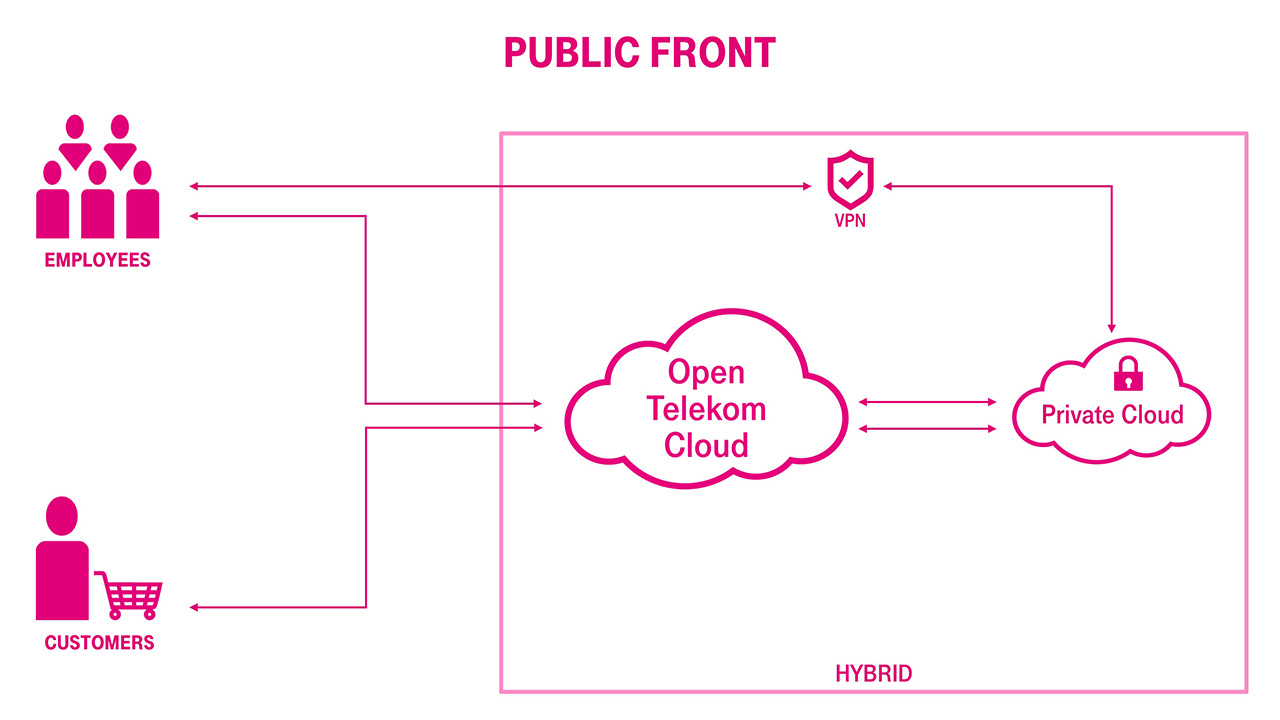
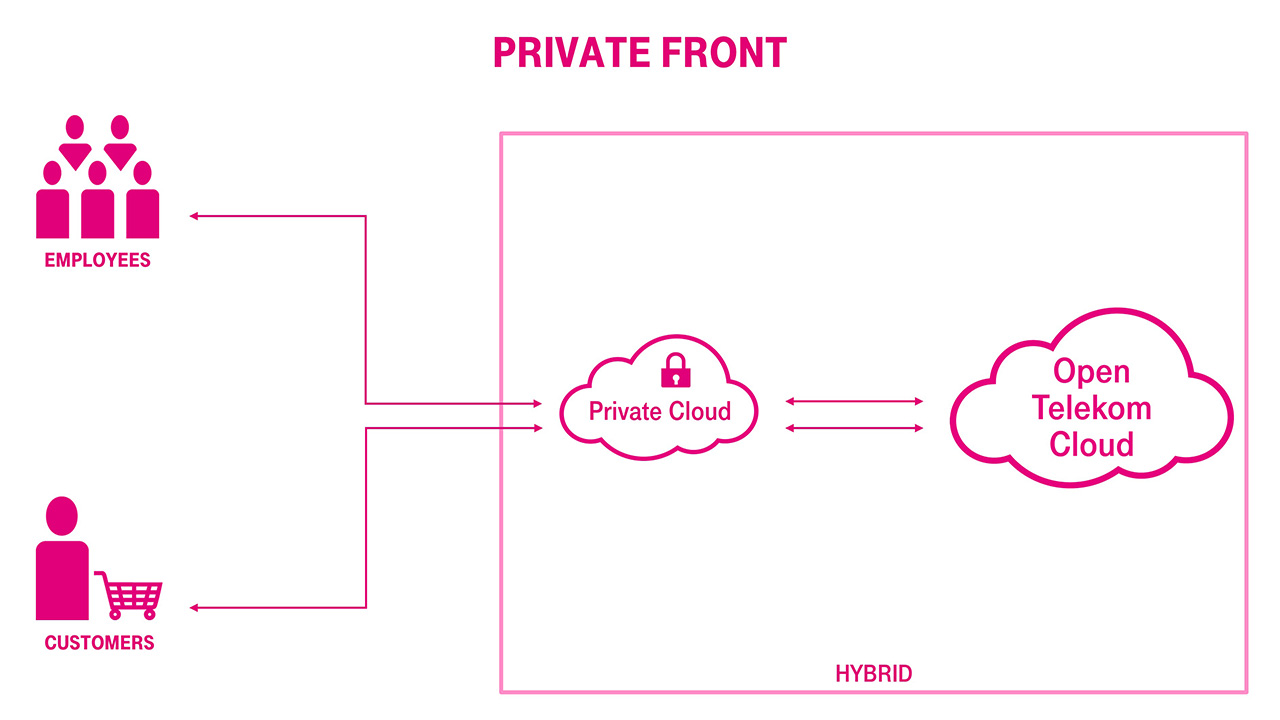
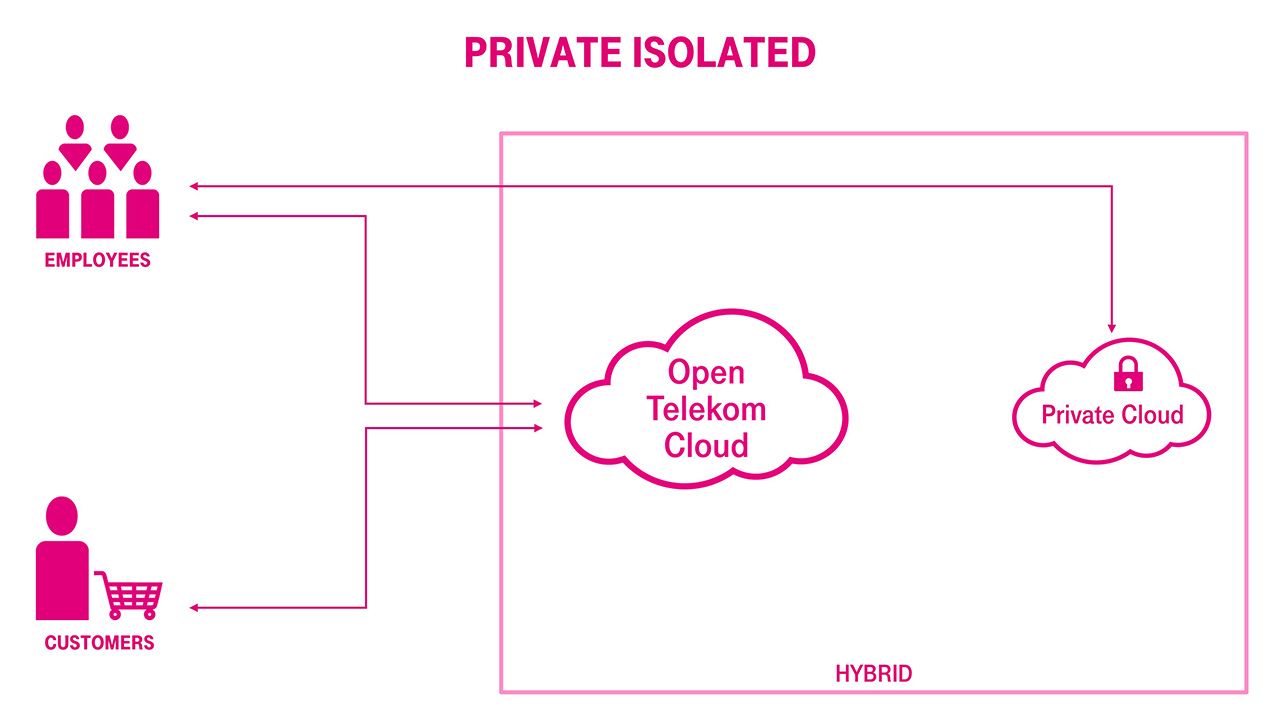
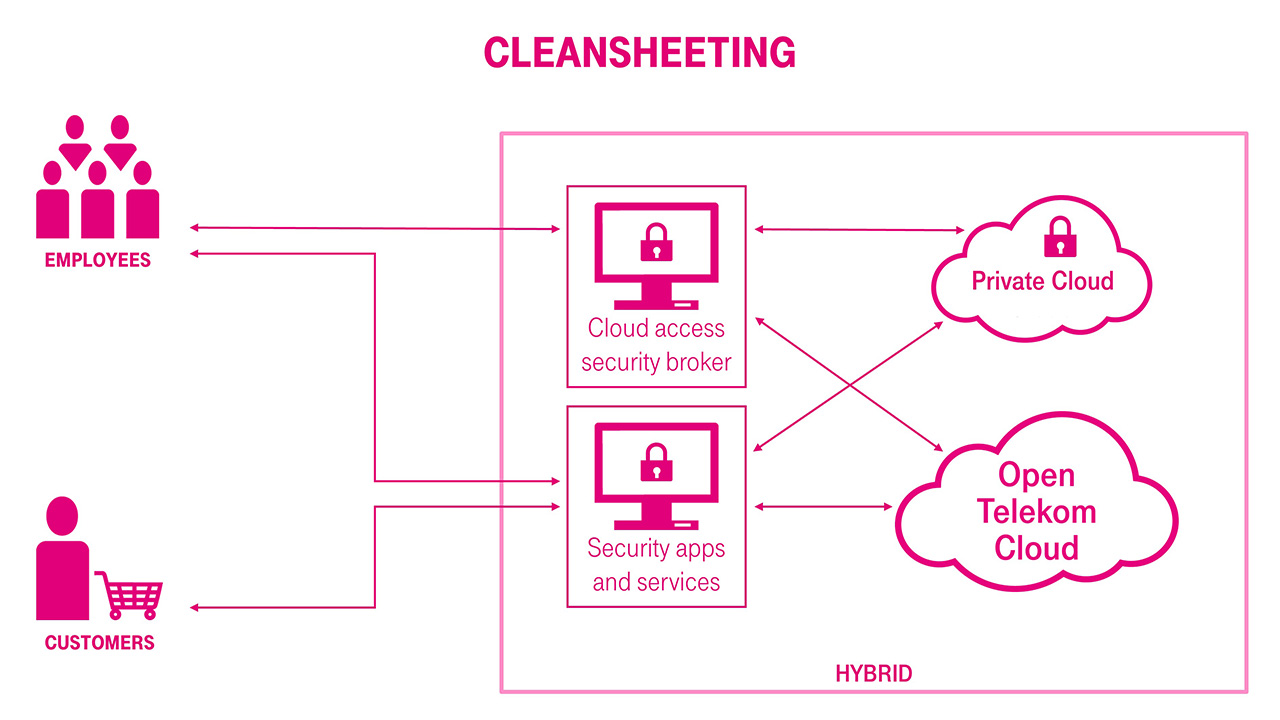
Companies need to balance costs against performance, complexity, security, and latency. The four most common topologies that enterprises can use to design hybrid cloud architectures are: public front, private front, private isolated and cleansheeting.